3 top enterprise file encryption programs compared
- 17 June, 2021 19:55

Large or small, every company has secrets it needs to keep to stay in business. It might be its customer list, proprietary source code, next-gen product plans or even the secret sauce for its sandwiches, but they all need to be protected from hackers, snoops and industrial spies. The best way to keep these things—and every other confidential item—under wraps is to hide them in plain sight by encrypting them.
The mathematical magic of encryption means that only those with the correct key can unscramble its contents and open the file. The odds are heavily stacked against a hacker randomly guessing the key or using the brute-force approach to crack the encryption key. Take the popular Advanced Encryption Standard as an example. Using the variant with a 256-bit decryption key, a.k.a. AES-256, an astounding 3 followed by 76 zeros possible keys are available. So, even with a break-in, your company’s data would remain secure because the encrypted files will remain unreadable to the intruders.
Encryption is becoming a popular way to protect company data. As recently as 2005, only about 15 per cent of US companies surveyed by the Ponemon Institute had an encryption strategy. In 2020, that figure was up to 48 per cent, with payment, financial, and personnel records the top choices for encryption. Still, it leaves the data at more than half of firms exposed and potentially unprotected.
Dozens of encryption packages are available, though many of the apps are aimed at consumers hiding compromising frat party pictures or legal documents. Others, like Microsoft’s BitLocker and Apple’s Data Vault, are meant for scrambling the entire disk of a computer, not individual files.
What to look for in a file encryption tool
First, a business-class encryption program has to, well, encrypt files efficiently, reliably, and quickly so that workers actually use it. If the app baulks at encrypting large files or doesn’t consistently decode them, it won’t be used and the firm’s data will be just as vulnerable as if it didn’t have the software.
The best encryption packages not only provide a choice of encryption method but can scramble individual files so that employees can safely send and share key data with colleagues. Some even provide a secure sharing method for coworkers to collaborate without risking the company’s secrets.
While encryption is a good way to secure files you want to keep, what about those you don’t want anymore? Deleting them only removes the drive’s FAT entry that points the processor to where its data is stored. The underlying data remains until it is overwritten by a new file. Shredding or wiping software that is sometimes included with an encryption app can make it literally disappear by repeatedly overwriting the data with a variety of patterns. It’s a nice bonus for the security minded.
Finally, think about key management. After all, it is the “key” to opening encrypted files, but if it’s not available or too available, you might be left with a false sense of security. Some packages keep their keys in the cloud while others store them locally. The best provide a recovery key that can help if a key is lost in a computer meltdown or the sudden departure of an employee, but it’s best if these are, you guessed it, encrypted.
Below are three of the best encryption programs aimed at enterprises that can encrypt individual files while managing the keys required to open the scrambled items. I gave each a workout that focused on ease of installation and use as well as how fast they encrypted and decrypted a folder containing 505MB of assorted data.
Boxcryptor Enterprise
By allowing the use of a wide variety of local and online storage systems, Boxcryptor Enterprise aims to protect a company’s data with industrial-strength encryption no matter where the data resides. With a focus on medium to large firms, Boxcryptor Enterprise customers include large universities and international firms with thousands of employees. One of its most prominent clients is a large German carmaker.
 Brian Nadel
Brian Nadel
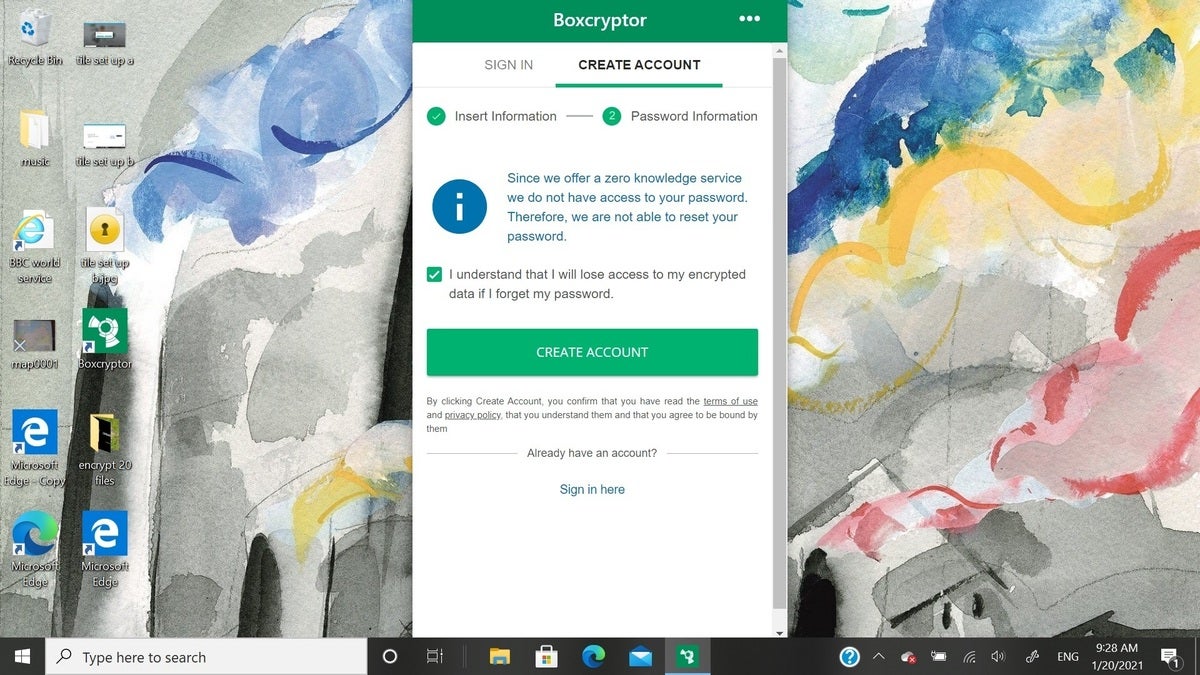
Boxcryptor create account
While the software lacks the ability to encrypt entire hard drives, it can protect the contents of files and folders. It is HIPAA and GDPR compliant and the company has a zero-knowledge philosophy with no backdoors or logs in its software. The Boxcryptor Enterprise version stores the needed encryption keys securely online and caches them locally as needed. It is the rare encryption software that includes the ability to set up two-factor authentication (2FA) as a further layer of protection.
 Brian Nadel
Brian Nadel
Boxcryptor dashboard
Unfortunately, it lacks the remote management capabilities that Jetico BestCrypt offers, but the Boxcryptor software can be remotely installed. An IT administrator can set up workgroups as well as company-wide encryption policies that can specify things like password length. A big bonus for large companies that use a variety of different platforms is that Boxcryptor covers the OS gamut with compatibility for Windows, MacOS and Linux systems as well as Android and iOS tablets and phones. Easily, the company has the widest offering.
The company’s latest effort is a version that works within Microsoft Teams to make collaboration more secure. It doesn’t encrypt the audio, video and chat, but scrambles any shared files in Teams online and automatically unscrambles them when needed.
In addition to local saving and using a flash drive, the program can encrypt files sent to OneDrive, Dropbox, GoogleDrive and Sharepoint servers. Unlike Nordlocker, Boxcryptor doesn’t offer online space for these files and lacks the ability to encrypt files directly from popular programs like Office.
Boxcryptor Enterprise uses AES-256 encryption to secure files or folders of any size in virtual drives but unlike the Jetico software, it doesn’t offer alternative ciphers. There’s no way to hide encrypted files behind a password for an extra layer of security.
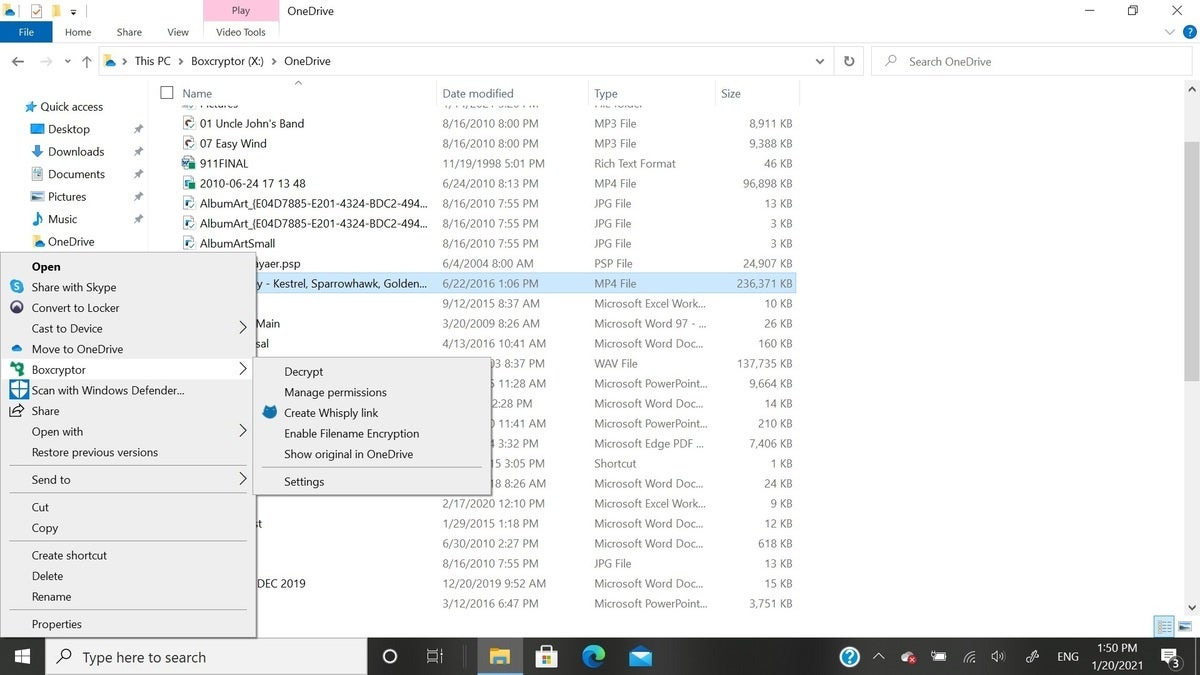
Under the surface, Boxcryptor keeps the encrypted files in virtual drives that are automatically created and can be of any size. Encrypted files have a green box added to the icon. Files can be encrypted and decrypted with a right-click in Windows Explorer or dragged to the encrypted drive. The originals are automatically wiped.
 Brian Nadel
Brian Nadel
Boxcryptor decrypt
It took me a little more than five minutes to install Boxcryptor on my HP EliteBook Dragonfly system. The program provides a warning that lost keys can’t be recovered. Unlike other encryption software, it works behind the scenes with little or no traditional interface. There is an online interface for doing things like exporting your encryption keys for central storage and setting up 2FA.
The Enterprise package includes Boxcryptor’s Whisply. This home-grown browser-based system offers a protected sharing platform that can help a group collaborate securely online. On the downside, none of Boxcryptor’s products include a file shredder.
All I had to do to encrypt my files was to drag them into the virtual X: drive that Boxcryptor set up for holding encrypted files. It encrypted my 505MB of test files in 4.1 seconds and reconstituted them in 2.9 seconds. All of the elements came through without a digital scratch.
Boxcryptor Enterprise sells an initial five-seat package for US$720 a year, or US$144 per user. A 1,000-seat company can expect to pay about US$108 per year per user on a three-year contract. Still, it’s one of the most expensive ways to protect a company’s data. There’s a free version to try out.
While it lacks a way to centrally manage a company’s encryption efforts, the combination of cross-platform support and a version that melds with Teams makes Boxcryptor Enterprise an innovative contender.
Rating: 4/5
Pros:
- Works with Windows, Mac, Linux, iOS and Android
- Microsoft Teams version
- Secure file sharing portal
Cons:
- Expensive
- No file Shredder
Jetico Enterprise Data Protection
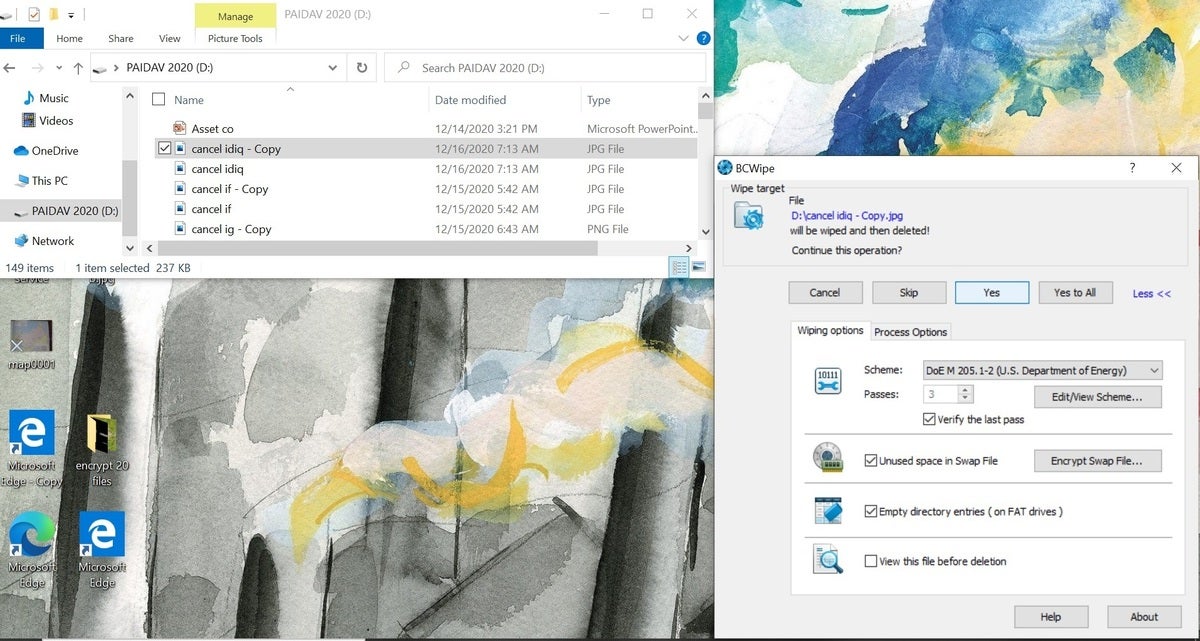
With the choice of two encryption and two shredding apps, Jetico Enterprise Data Protection has an a la carte menu so you don’t get—and pay for—more than your company needs. The combination of the company’s BestCrypt encryption and BCWipe shredding makes for a formidable combination for the security minded.
Jetico’s security offerings come down to whether you want to encrypt or fully erase a complete hard drive (with BestCrypt Volume Encryption and BCWipe Total Wipe Out) or work file by file (with BestCrypt Container Encryption and BCWipe). By contrast, competitors, like NordLocker and BoxCryptor lack the file shredding potential of BCWipe.
 Brian Nadel
Brian Nadel
Jetico BCWipe tool
The software is compliant with HIPAA, GDPR and the payments-oriented PCI DSS standard. The company focuses on securing the data held by governments, national laboratories and medium to large enterprises, including the US Department of Defense. Jetico has built its encryption programs without backdoors or external logging, but that also means that if a key is lost, so is the data. It has released its source code to the public.
Read more on the next page...
Page Break
BestCrypt Volume Encryption can scramble entire drives with the choice of five encryption ciphers that range from AES to Camellia. By contrast, the BestCrypt Container Encryption works on individual files and adds three more choices, including the Blowfish, CAST and Camellia ciphers. Meanwhile, BC Wipe offers the choice of 14 techniques to permanently remove any trace the file ever existed.
 Brian Nadel
Brian Nadel
Jetico encryption options
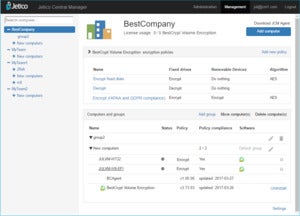
A big step forward for businesses is the ability to install and manage BestCrypt remotely and update the software without the user even knowing about it. For example, an IT or security manager can specify the level of encryption for a single, group or all computers in company’s digital fleet. The Central Manager software also has a place to store encrypted recovery keys just in case an employee loses the key or abruptly leaves the company. Files can also be remotely wiped through the dashboard.
 Brian Nadel
Brian Nadel
Jetico Central Manager
Unlike competitors that only cater to PCs and Macs, Jetico BestCrypt works with Linux computers as well as Android phones and tablets. Unlike Boxcryptor, there are no encryption apps for iPhones or iPads, however.
BestCrypt Container Encryption creates a virtual drive and takes a minute to set up. A twist is that as the drive is created, you need to either randomly tap the keyboard or move the mouse around to create data that is used to make the keys. There’s no limit to the number or size of these containers, as long as there’s storage space available, and the container can be set to automatically expand to fit even the largest files.
Unlike many competitors, BestCrypt can add a layer of security by hiding or masking the encrypted container so that outsiders don’t even know it’s there. A hidden container only comes to the surface when the correct password is entered.
BestCrypt’s interface is functional and easy to learn to use on a daily basis. On the downside, all the program’s major elements have separate interfaces. The program lets you scramble or wipe a file or folder with the right click on the Windows Explorer. Unfortunately, you can’t encrypt files from within popular programs, such as Office.
On top of saving files locally or to external drives, including a USB flash drive, BestCrypt works with online storage systems like OneDrive and Box. An administrator can set up group containers online that allow employees to save and update files online, but Jetico doesn’t offer online storage space to users.
Installing and using Jetico’s encryption is a little more complicated but its support pages have detailed instructions and videos that can be distributed as an aid to training users. It took me a little more than four minutes to install the program on my HP EliteBook Dragonfly notebook. The program took 1.3 seconds to encrypt my folder of 505MB worth of assorted files. The interface gives the option of automatically or manually wiping the original file, which took an additional 5 seconds. Later, I was able to unscramble them in 2.5 seconds; all the files were readable.
Jetico sells its four security products on their own, but I got the bundle of its three most popular products—BestCrypt Volume Encryption, BestCrypt Container Encryption and BCWipe—as a package for US$220. An organisation with 1,000 seats would pay US$65,890 for a site licence for the first year. After that, the price is halved to US$32,945 per year for support, updates, and any new versions, making it one of the most inexpensive ways to protect data. At about US$33 per user, it’s a bargain.
With a focus firmly on end-to-end data security, Jetico Enterprise Data Protection can inexpensively keep all your company’s secrets.
Rating: 4.5/5
Pros:
- Includes encryption and shredding apps
- Central Management console
- Works with PCs, Macs, Linux, and Android
- Good volume pricing
Cons:
- Program elements could be more integrated
- No app for iOS systems
NordLocker for Business
With a focus on small and medium firms, NordLocker puts an emphasis on security, ease of use, and not having to train staff to use it. With heavy-duty encryption behind the scenes, the program can secure a key file in the research lab or the CFO’s entire hard drive.
Used daily by a variety of companies that specialise in finance, healthcare and education, NordLocker is HIPAA- and GDPR-compliant. The company’s zero-knowledge policy means that NordLocker doesn’t keep logs of your company’s encryption activity or keys. This helps with anonymity but can’t help with a lost encryption key.
It was quick and easy to install the program on my HP EliteBook Dragonfly laptop and in 1 minute and 18 seconds I was encrypting like a pro. There’s no way to remotely install or manage the program, but the company’s engineers are working on adding this feature. The program keeps its encryption keys locally and creates a recovery key just in case the master key is lost or an employee leaves the company. Needless to say, the company’s IT administrator or CSO needs to keep this data under lock and key.
 Brian Nadel
Brian Nadel
NordLocker application lockout settings
Soon, I was encrypting and decrypting files right and left. NordLocker uses AES-256 and only works with 64-bit PCs and Macs. Unlike Jetico’s BestCrypt, there are no apps for Linux, Android, or iOS, but the company is planning to introduce mobile encryption apps later this year.
Organised around containers called Lockers, encrypted folders can be as small or large as you like. NordLocker’s clean and spare interface makes using it second nature but the dark look can seem ominous. Its Windows-Explorer-like listing of available files on the left and NordLocker’s icon on the right made it easy to drag files to have them encrypted. Alternatively, a right click on the Windows Explorer’s interface gets the encryption ball rolling. All original files are wiped from the system.
 Brian Nadel
Brian Nadel
NordLocker folder interface
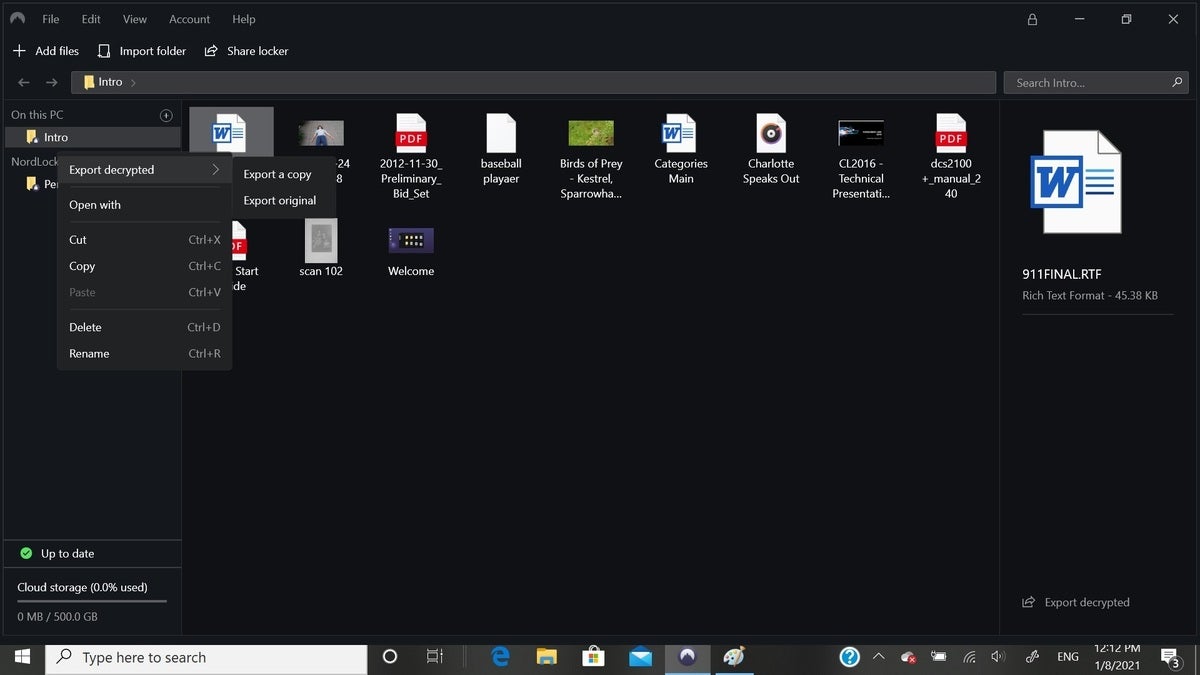
Once scrambled, encrypted files show the company’s mountain logo, have a .locker extension and are visible. The software can neither hide files behind a password nor save and encrypt files from within major apps, like Office.
NordLocker can encrypt files locally, to an external drive, or online. Business users get 500GB of secure storage space per account and the system is integrated with Dropbox and Google Drive. NordLocker allows users to give others at work permission to view and alter any encrypted files or folders by using its Share function. Unfortunately, there’s no file shredder for making files disappear.
 Brian Nadel
Brian Nadel
NordLocker folder export
Once everything was set up and operating, it took 1.8 seconds to encrypt a folder containing 10 files that added up to 505MB and included documents, images, and video. For the most part when it’s time to open the file, there’s no manual decryption because the files are automatically decrypted and available until a time out is reached; this can be set manually from 1 minute to 1 hour. It took 3.0 seconds to decrypt and open the folder when logged out. All the files came through without a problem.
At US$48 a year for the first seat with 500GB of online storage space, NordLocker is inexpensive and the company offers a free version. While NordLocker lacks a trial period, you can get a full refund after up to 30 days. Between 10 per cent and 50 per cent volume discounts are available and the company is working on a bundle that combines the encryption program with the company’s password manager and global VPN network to create a one-stop security centre.
Rating: 4.0/5
Pros:
- Easy to use
- Inexpensive
- Includes file sharing portal
Cons:
- No file shredder
- PCs and Macs only

